In hoax.tech, various black page action types are implemented.
The Set Cookie action type is not intended for automatic redirection to a black page; it is used to set a cookie containing the flow hash for targeted visitors identified as non-bots, and to trigger a subsequent specified action.
¶ How the Set Cookie action type works
- All visitors, including the targeted audience, remain on the white page.
- Targeted visitors — users identified as non-bots and matching the flow conditions — receive a cookie (the hash of the integrated flow).
- An event is added on the white page that checks for the presence of the cookie (i.e., verifies the visitor is not a bot).
Example events:
- clicking a Cookie Consent button
- navigating via a link or opening a specific page
- clicking a file download button
- scrolling the white page
- reaching a specified time threshold
- and other actions
- After the event occurs, the following options are possible:
- the targeted audience is redirected to the black page
- part of the white page content is modified to display to the targeted audience
- the targeted audience receives an executable file
- other preconfigured actions are executed
Bots and moderators who do not have the cookie when performing the same action:
- will not trigger any changes and remain on the white page
- may be redirected to a second white page
- may receive a different, safe file
¶ Setting up the Set Cookie action — step-by-step example
Let’s go through an example of using the Set Cookie action type to redirect targeted visitors after they click a button.
In this case, users identified as non-bots will be redirected to the black page, while bots and moderators will be sent to a second white page.
Step 1. Create and configure a flow.
You can enter any URL as the black page link, since with the Set Cookie action type, no automatic redirection to the black page occurs.
Step 2. In the integration settings, set the Set Cookie action type.
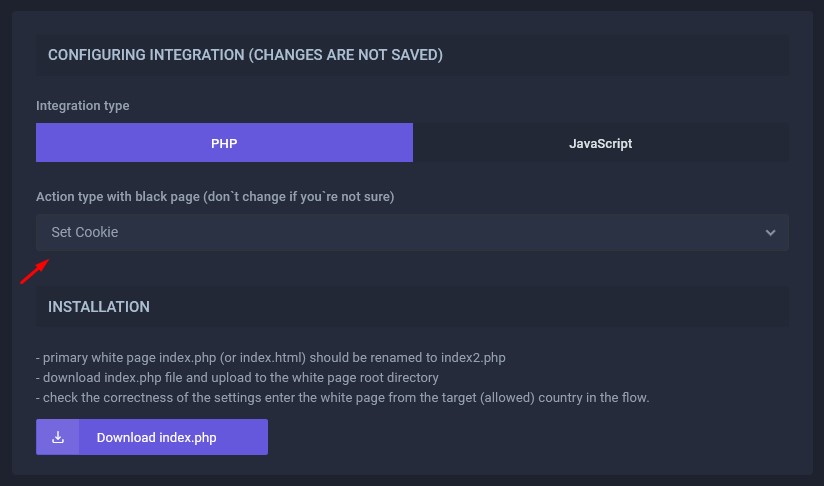
Step 3. Integrate the cloaking script into the white page (https://setcookie.hoax.tech) using the standard PHP integration method:
- Download the integration file
index.php - Rename the main white page file
index.phptoindex2.php(if the main file has a.htmlextension, rename it toindex2.phpwith changing extension to.php) - Upload the downloaded
index.phpfile from the flow to the root directory of your website
After sending traffic to the white page, both bots and real visitors will remain on the same page — however, real visitors will receive a cookie containing the flow hash.
Step 4. Embed the following script into the To Rent button located on the white page.
The next script, which we will integrate into the "To Rent" button on the white page
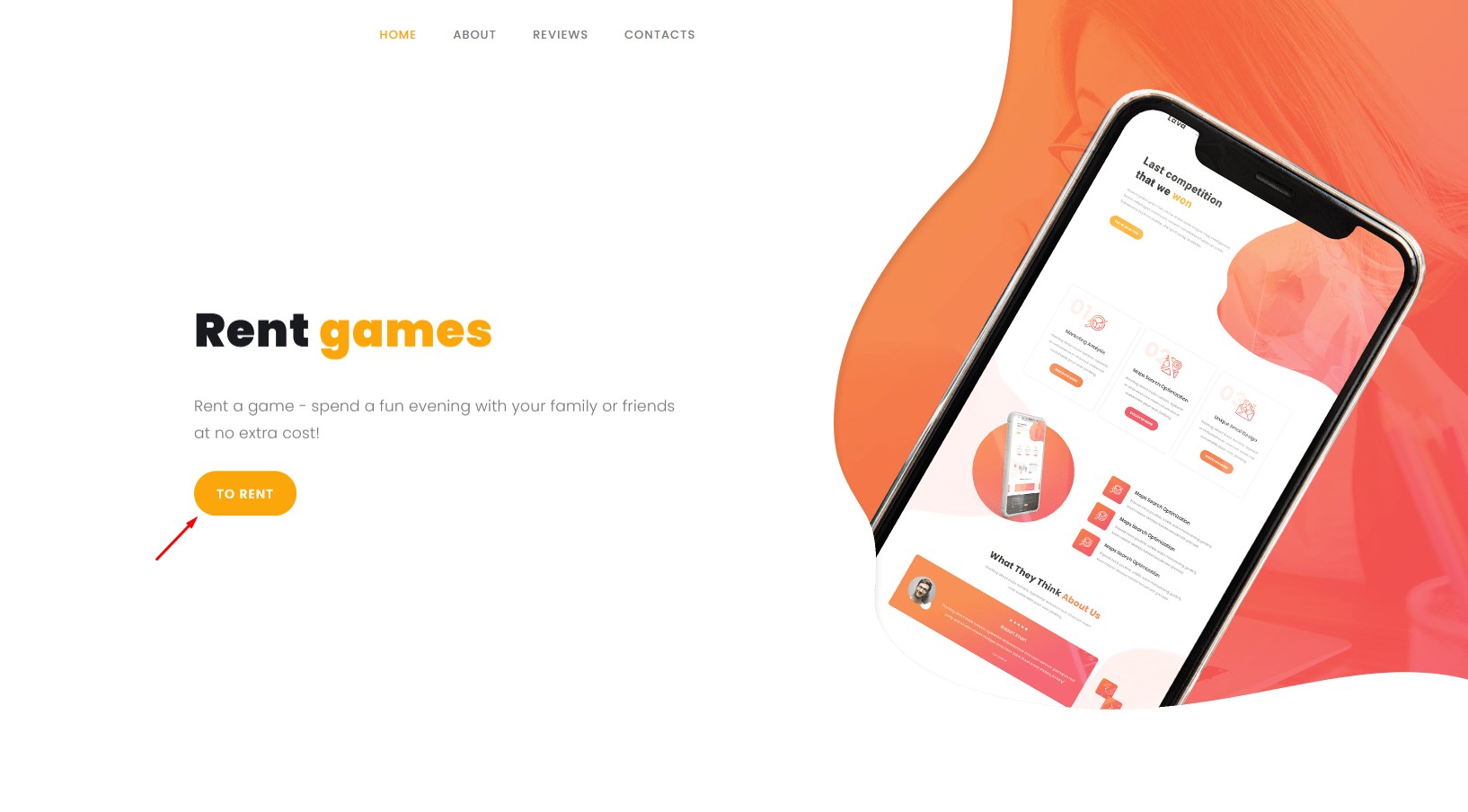
It will check for the presence of the cookie for users who click the button and redirect:
- targeted visitors to the black page
- bots, moderators, and other visitors to the secondary white page (in our case — https://setcookie.hoax.tech/contact-us)
document.querySelector("#BUTTON").addEventListener("click", function() {
function getCookie(name) {
const matches = document.cookie.match(new RegExp(
"(?:^|; )" + name.replace(/([.$?*|{}()[]\/+^])/g, '\\$1') + "=([^;]*)"
));
return matches ? decodeURIComponent(matches[1]) : null;
}
if (getCookie("FLOW_HASH")) {
window.location.href = atob("BASE64_BLACK_PAGE");
} else {
window.location.href = atob("BASE64_WHITE_PAGE");
}
});
Variables:
BUTTON — the ID of the button that triggers the event.
FLOW_HASH — the hash of the flow integrated on the white page. You can copy it from the Flows section (https://hoax.tech/flows) or directly from the browser’s address bar while editing the flow.
BASE64_BLACK_PAGE — the black page URL encoded in Base64 format.
BASE64_WHITE_PAGE — the white page URL encoded in Base64 format.
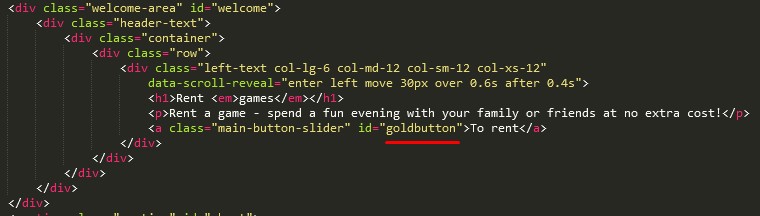
Step 5. Find the button ID in the white page code and copy it.
If the button doesn’t have an ID, assign any custom one — for example, goldbutton.
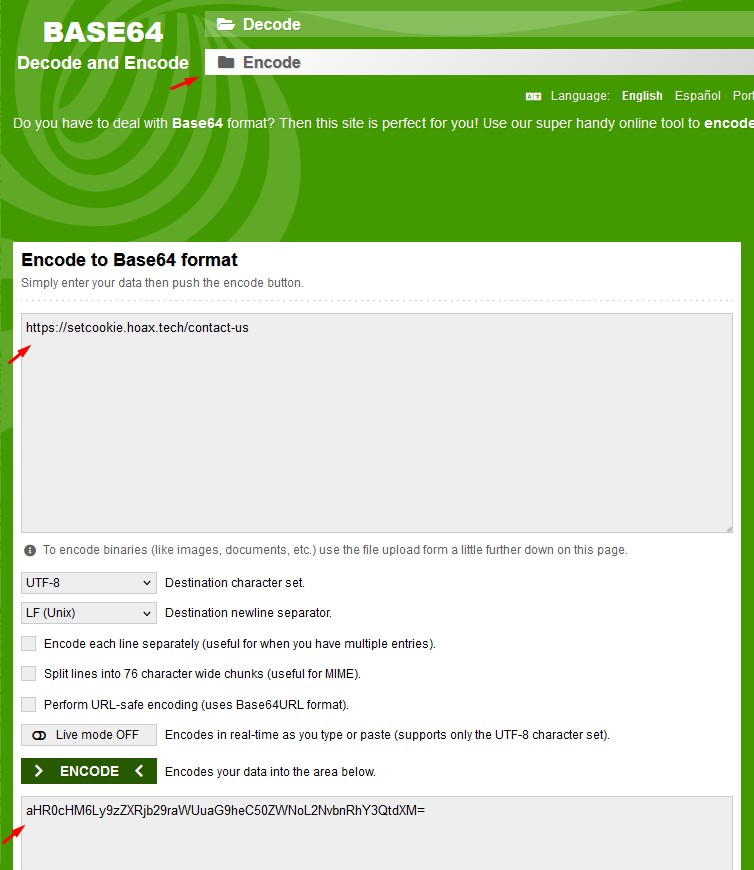
Step 6. For better security, encode the URLs in Base64 format.
You can use a service like base64decode.org
Step 7. Add all the variables to the code.
It should look like this:
document.querySelector("#goldbutton").addEventListener("click", function() {
function getCookie(name) {
const matches = document.cookie.match(new RegExp(
"(?:^|; )" + name.replace(/([.$?*|{}()[]\/+^])/g, '\\$1') + "=([^;]*)"
));
return matches ? decodeURIComponent(matches[1]) : null;
}
if (getCookie("4126123ffb74b745e81c70f3bfb686df")) {
window.location.href = atob("aHR0cHM6Ly9ibGFjay5ob2F4LnRlY2g=");
} else {
window.location.href = atob("aHR0cHM6Ly9zZXRjb29raWUuaG9heC50ZWNoL2NvbnRhY3QtdXM=");
}
});
Step 8. Add the resulting script to the bottom of the white page executable file (index2.php), placing it between the <script> and </script> tags:
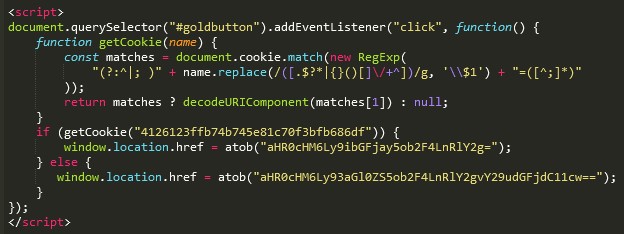
Step 9. Save the file.
You can also obfuscate the JS script to prevent ad-network crawlers from determining its purpose. You can use the service https://obfuscator.io/
Result:
function _0x44c4(){const _0xe4c0fc=['403347WWuKVP','8fEDpfp','27072aUCRWv','aHR0cHM6Ly9ibGFjay5ob2F4LnRlY2g=','addEventListener','9391824hodZYU','3726506YANKlF','4126123ffb74b745e81c70f3bfb686df','aHR0cHM6Ly9zZXRjb29raWUuaG9heC50ZWNoL2NvbnRhY3QtdXM=','768945BCWBCp','#goldbutton','1460530wQGfLy','8pIPjbO','href','click','(?:^|;\x20)','3695868Lymavf','location','replace','querySelector'];_0x44c4=function(){return _0xe4c0fc;};return _0x44c4();}function _0x21a8(_0x3ae868,_0x451a7c){const _0x44c499=_0x44c4();return _0x21a8=function(_0x21a859,_0xadcba8){_0x21a859=_0x21a859-0x18e;let _0x236e1f=_0x44c499[_0x21a859];return _0x236e1f;},_0x21a8(_0x3ae868,_0x451a7c);}const _0xed30a5=_0x21a8;(function(_0x37da8d,_0x52157d){const _0x4c2e78=_0x21a8,_0x43e449=_0x37da8d();while(!![]){try{const _0xda49f9=-parseInt(_0x4c2e78(0x19b))/0x1+parseInt(_0x4c2e78(0x19d))/0x2+parseInt(_0x4c2e78(0x190))/0x3*(parseInt(_0x4c2e78(0x193))/0x4)+parseInt(_0x4c2e78(0x192))/0x5+-parseInt(_0x4c2e78(0x197))/0x6+parseInt(_0x4c2e78(0x1a1))/0x7*(-parseInt(_0x4c2e78(0x19c))/0x8)+parseInt(_0x4c2e78(0x1a0))/0x9;if(_0xda49f9===_0x52157d)break;else _0x43e449['push'](_0x43e449['shift']());}catch(_0x107c00){_0x43e449['push'](_0x43e449['shift']());}}}(_0x44c4,0x4bb6d),document[_0xed30a5(0x19a)](_0xed30a5(0x191))[_0xed30a5(0x19f)](_0xed30a5(0x195),function(){const _0x8a7688=_0xed30a5;function _0x4d91d4(_0x1cc909){const _0x113a72=_0x21a8,_0x31c119=document['cookie']['match'](new RegExp(_0x113a72(0x196)+_0x1cc909[_0x113a72(0x199)](/([.$?*|{}()[]\/+^])/g,'\x5c$1')+'=([^;]*)'));return _0x31c119?decodeURIComponent(_0x31c119[0x1]):null;}_0x4d91d4(_0x8a7688(0x18e))?window[_0x8a7688(0x198)][_0x8a7688(0x194)]=atob(_0x8a7688(0x19e)):window[_0x8a7688(0x198)][_0x8a7688(0x194)]=atob(_0x8a7688(0x18f));}));
Setup is complete.
Here is an example script where targeted visitors will be redirected to the black page, while for bots and moderators, the button will simply not work. In this case, a second white page is not required.
document.querySelector("#BUTTON").addEventListener("click", function() {
function getCookie(name) {
const matches = document.cookie.match(new RegExp(
"(?:^|; )" + name.replace(/([.$?*|{}()[]\/+^])/g, '\\$1') + "=([^;]*)"
));
return matches ? decodeURIComponent(matches[1]) : null;
}
if (getCookie("FLOW_HASH")) {
window.location.href = atob("BASE64_BLACK_PAGE");
}
});